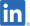Estimated reading time: 10 minutes
One click. That’s all it takes for a hacker to turn your business into a weapon against your clients.
Attacks like these are no longer just a “big business” problem. Hackers have leveled up; now, they aim straight at small and mid-sized businesses.
Phishing emails. Smishing texts. They look legit. They feel real. But they’re crafted to steal your logins, hijack your accounts, impersonate your business, and make you the face of the scam.
If you run an appointment-based business, this hits harder. Because this isn’t just about tech, it’s about trust. If hackers gain access to the communication platforms you use to communicate with your clients, all it takes is one spoofed message from your business email or number.
Boom. Your clients get burned. Your reputation? Toast.
Here’s what these attacks look like, how they spread, and what you (and Apptoto) can do to shut them down right now.
What Are Phishing and Smishing Attacks?
Phishing and smishing are deceptive scams that trick you into giving up sensitive information. This could include usernames, passwords, or credit card numbers that attackers use to access your accounts.
Phishing (Email-Based Attacks)

Phishing attacks are fake emails that look like they come from a trusted source: your bank, a favorite retailer, or even a team member. The goal is to get you to click a malicious link or enter your login credentials into a fake website.
Hackers will even mimic the look and feel of real emails from trusted brands (logos, layouts, even sender names), but there are usually a few red flags if you know what to look for.
Watch out for:
Display Name Trickery:
An email claims to be from “Apple Support,” but the email address is applehelp12345@hotmail.com.
Fake Security Alerts:
“Your Apptoto account has been suspended. Log in now to restore access.” (link leads to a fake site)
Grammatical Errors and Typos:
“Dear User, your account are in dangerous. Please click here to safe it.”
Payment Information “Problems”:
Messages claim there is an issue with your payment details and urge you to update them, or face consequences.
Urgent Tone:
Messages that scare you into acting quickly are a major red flag.
Include Suspect Attachments:
Emails include unexpected invoices or files for software you never purchased. Opening these emails triggers malware downloads.
Smishing (Text-Based Attacks)
Smishing attacks use SMS to create a false sense of urgency or authority. These messages might appear to come from a known company or government agency, pushing you to click a suspicious link.

Example Smishing Scams:
- “This is the DMV. You owe a fine. Pay now to avoid license suspension: [malicious link]”
- “We noticed unusual login activity on your account. Secure your account now: [phishing URL]”
- “Hi, this is Dr. Smith’s office. Your latest payment failed to process, and we need you to update your credit card information immediately. Visit our payment portal.”
These scams are effective because they feel urgent and look legitimate, especially on mobile, where verifying senders is harder.
Phishing and Smishing Attacks in the Wild: Would You Fall for These?
Hackers are getting more sophisticated and more convincing. Below are real-world examples of phishing emails and smishing texts that have recently targeted businesses like yours, so you know exactly what to look for.
| Red Flag | Phishing Example (Email) | Smishing Example (Text Message) |
|---|---|---|
| Fake Sender Name | “Apple Support” name, but the email is applehelp12345@hotmail.com | “Your bank” texts you, but the number is from a generic local area code |
| Urgent Language | “Act now or your account will be deleted!” | “You owe a $150 fine. Pay now to avoid license suspension.” |
| Strange URLs | Hover over link → goes to facebook-login-alerts.com | Link says facebook.com but points to a shortlink or an unknown domain |
| Generic Greeting / Poor Grammar | “Dear User, please verify your informations to avoid suspension.” | “Hi. This link to payment. Click fast: [suspicious URL]” |
| Unexpected Attachments or Requests | Asks for billing info, password, or has a random attachment | Asks you to confirm personal details or download a file |
| Spoofed Security Alerts | “We detected a new device. Log in to secure your account.” | “Your Amazon Prime account has been locked. Tap here to unlock.” |
Free Gift
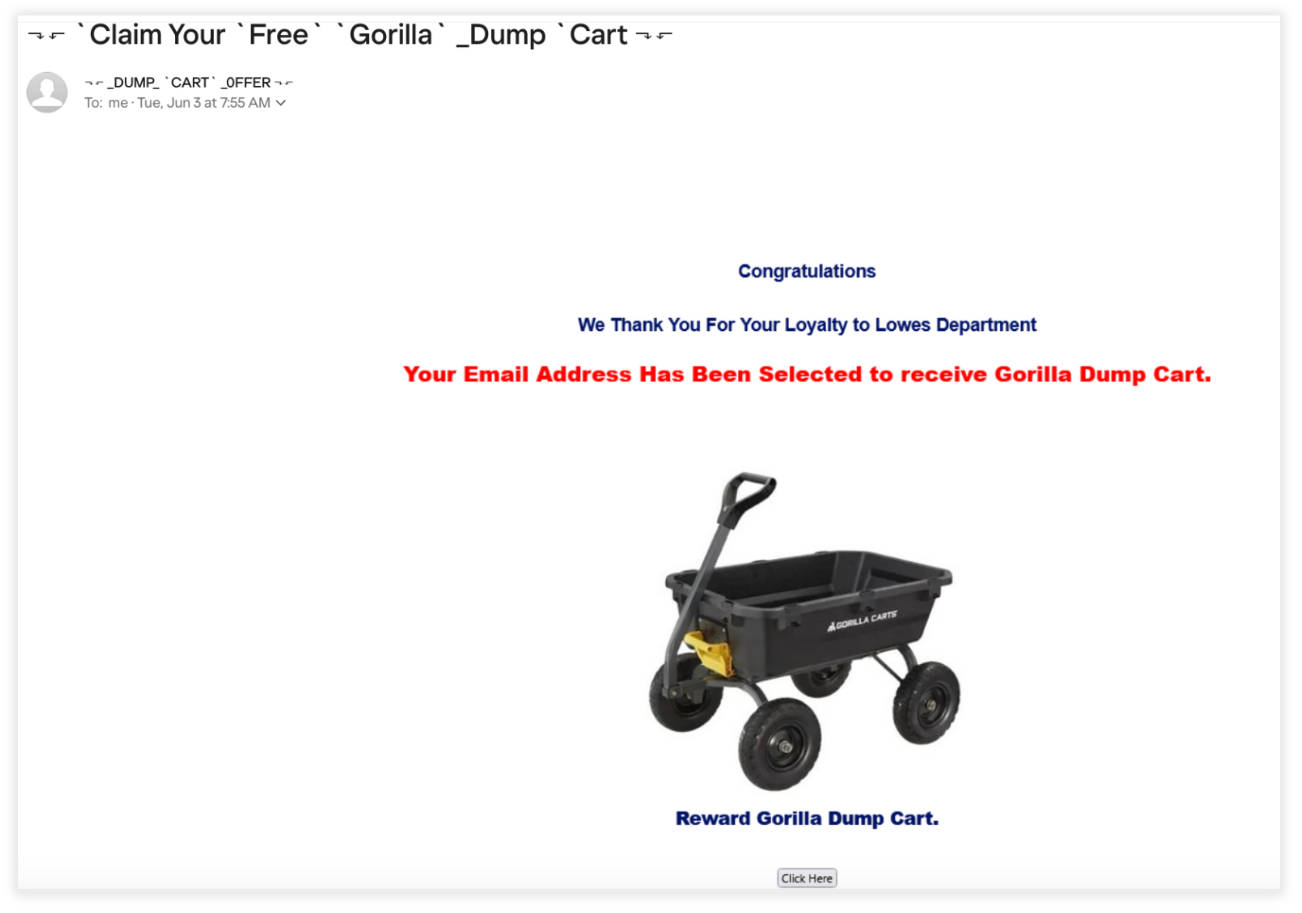
Payment Declined /Account Deactivation
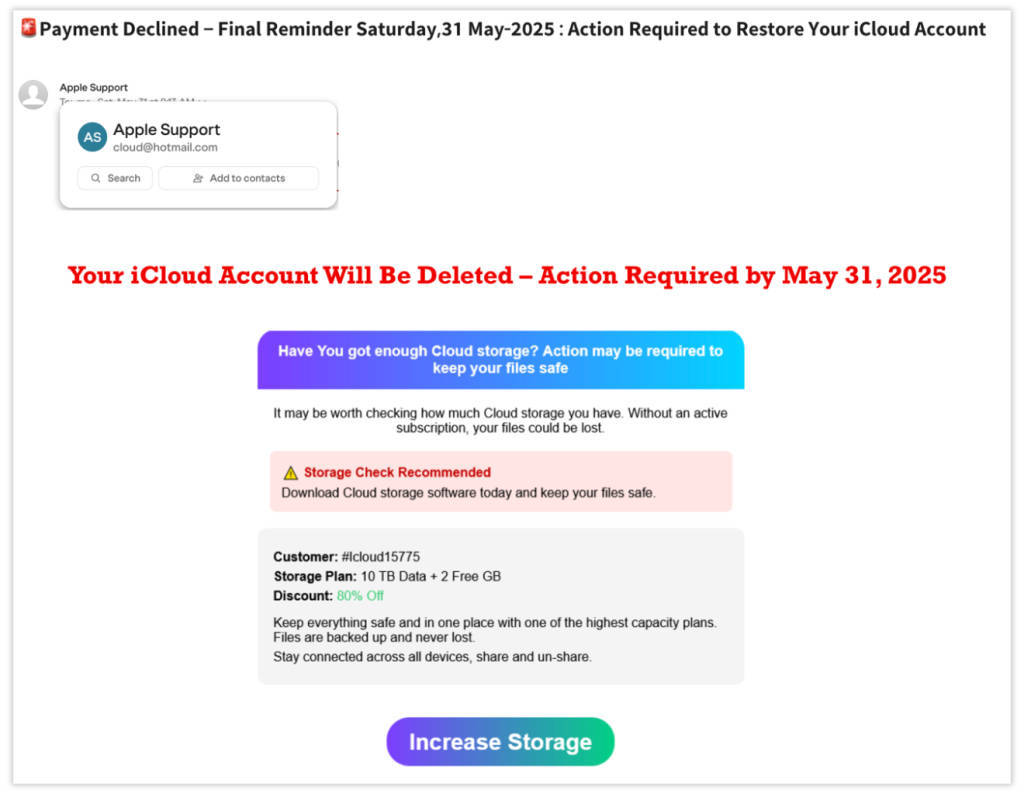
Job Offer
DMV tickets you need to pay
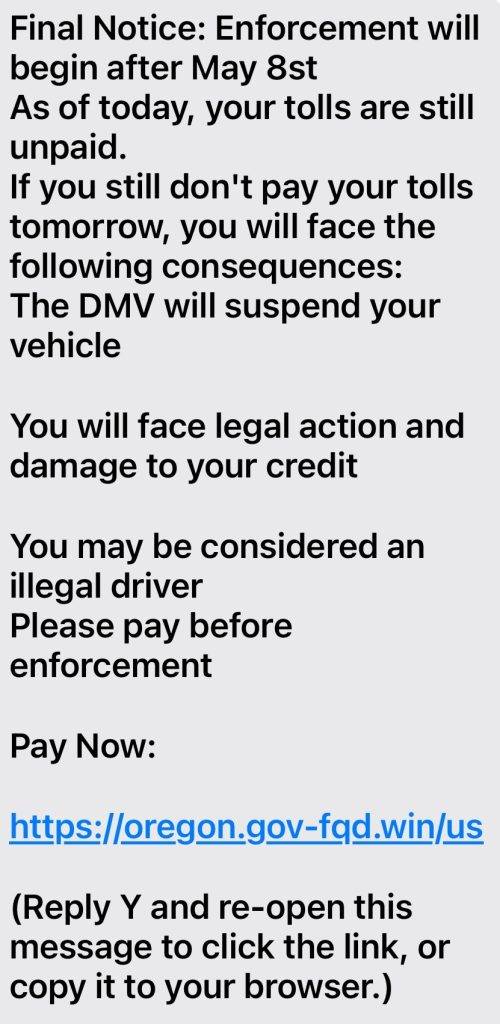
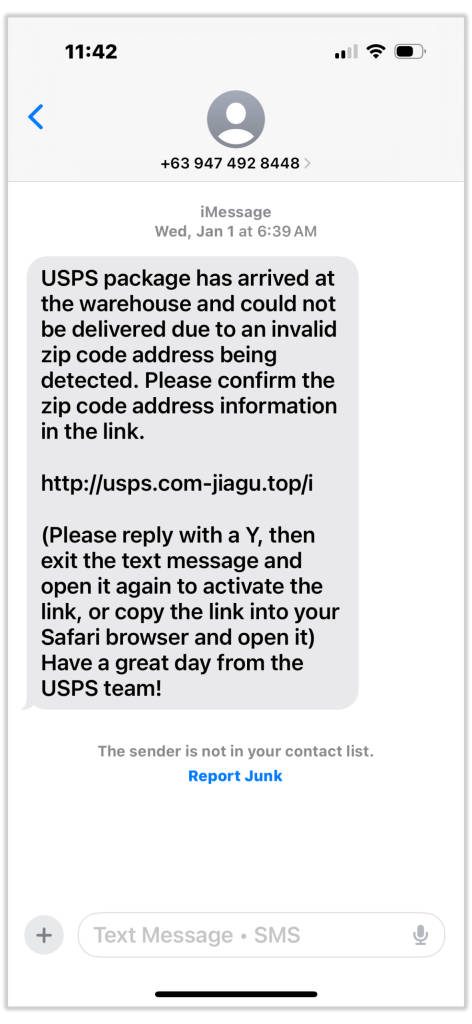
Fake package delivery issues
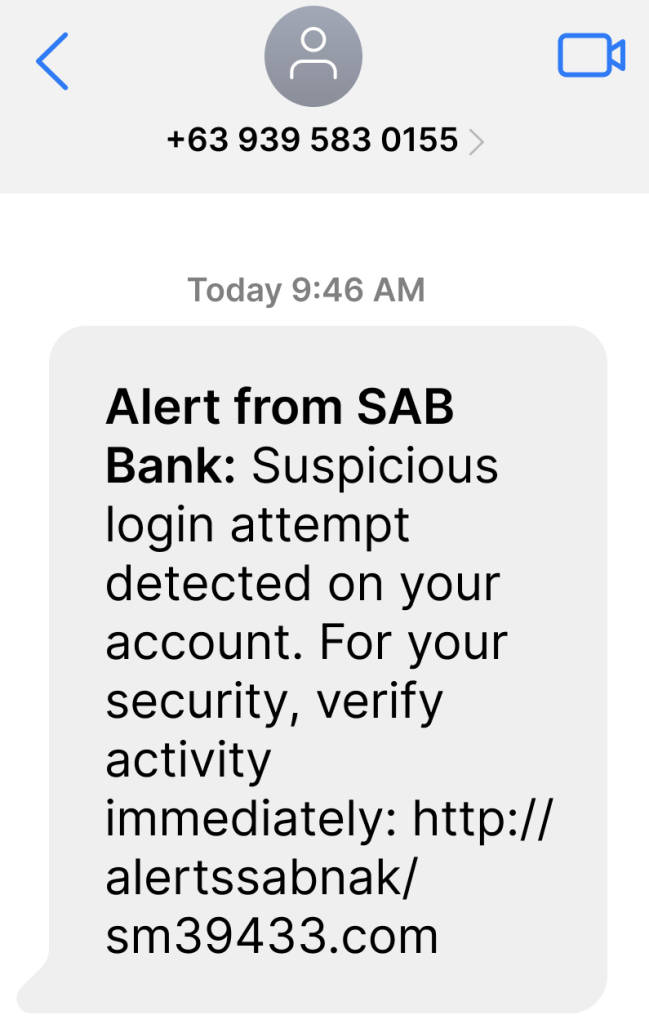
Bank alerts
Refund pending

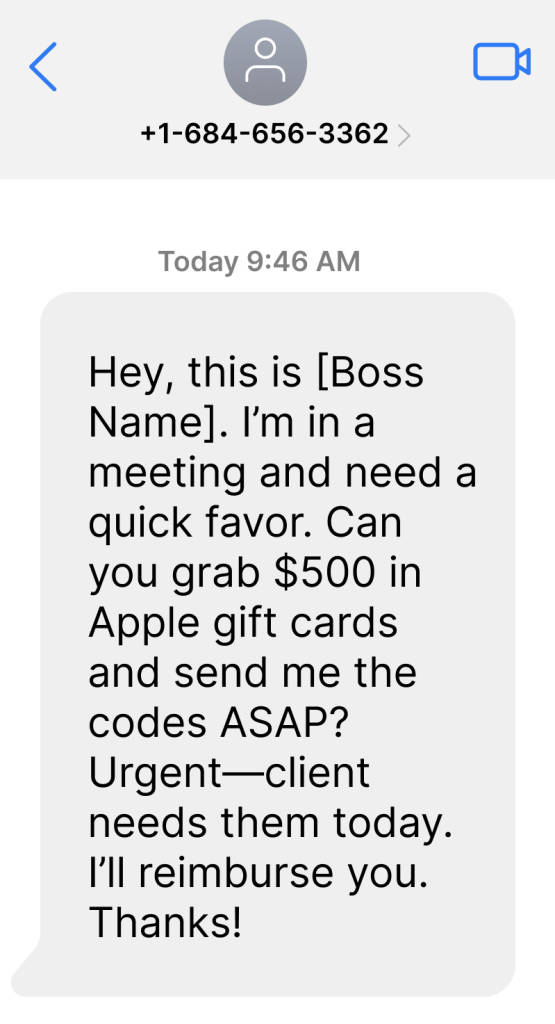
Gift Card Requests from “Boss”/”Coworker”
Why Appointment-Based Businesses Should Protect Against Phishing Attacks
Your business software keeps everything running—helping you operate, connect with clients, collect payments, and communicate. When hackers gain access to any of these platforms, they’re not just tweaking settings to cause a headache. They’re using your tools, name, and channels to launch attacks.
With communication platforms like Apptoto, one compromised account can turn your business into a convincing front for phishing scams, putting your clients, reputation, and bottom line at risk.
Hijacked Accounts Look Legit
If someone gains access to business messaging platforms like Apptoto, they can send emails and texts that appear 100% legitimate:
- The messages come from your real business number or email
- The client’s name and appointment info can be pulled from your calendar
- There are no visible signs to your clients that anything is wrong
From your client’s perspective, it looks like you’re the one asking for:
- Payment details
- Insurance information
- Social Security numbers
- Financial documents
- Link clicks
You Could Be On the Hook for the Damage
When this happens:
- Message costs skyrocket: Hackers can send hundreds (even thousands) of messages, and you’re the one billed for it.
- Client trust breaks instantly: Even one spoofed message asking for a credit card can result in furious phone calls and canceled appointments.
- Carriers may block your number: If spam or phishing messages are reported, your business number could be blocked by carriers or marked as spam, stopping your real messages from getting through.
- Reputation damage spreads fast: Clients may warn others online or leave negative reviews, thinking you were behind the scam.
Real Talk: It Isn’t Just a Technical Problem
It is a business continuity issue:
- Carriers may prevent your appointment reminders from being delivered
- Staff may spend days fielding angry calls and fixing confusion
- Revenue drops if you can’t reliably reach your clients
- Sensitive client data could be exposed, triggering HIPAA violations or other legal fallout
How Apptoto Helps Protect You
Apptoto has multiple layers of built-in protection to help proactively prevent account abuse and stop suspicious activity:

- Email Authentication (Login): Users without 2FA must enter a one-time code sent to their email each time they log in. Attackers have a harder time accessing your Apptoto account (even if they’ve stolen your password) since they’d also need access to your email.
- Email Authentication (Sending): For sending email, Apptoto supports SPF, DKIM, and DMARC to prevent spoofing and improve deliverability.
- Two-Factor Authentication (2FA): Extra login security that sends you a one-time code via text or an authentication app.
- Spam & Abuse Detection: Flags high-risk or spam-like messages before they go out.
- Login Activity Monitoring: Detects and alerts the team to strange login behavior.
- Rate Limiting: Prevents rapid sending of messages that could indicate a compromised account.
- SOC 2 Type 2 Certified: Apptoto meets strict industry standards for security, availability, and confidentiality, so you can trust that your data (and your clients’ data) is protected at every level.
We’re actively monitoring to keep your account safe, but strong habits on your end matter just as much.
Best Practices to Protect Your Business
✅ Don’t Share Logins
Give each team member their own Apptoto login. It’s safer and easier to manage access or remove users when needed. Plus, you avoid issues with Apptoto’s authentication requirements (e.g., when 10 people share a login, but all verification codes go to one person’s email
🔐 Use a Password Manager
Use tools like 1Password or LastPass to create and store strong, unique passwords you won’t forget (and attackers won’t guess).
📲 Enable 2FA for All Users
Set up two-factor authentication via SMS or an app like Google Authenticator. This stops most attacks even if a password is compromised.
🧠 Educate Your Team
Make sure everyone knows the signs of phishing and smishing. One careless click is all it takes.
🚫 Avoid Clicking Suspicious Links
Don’t trust links in unexpected emails or texts, especially ones urging you to act quickly. Go directly to the website instead.
🚮 Delete Suspicious Texts and Emails Immediately
If something feels off, trust your gut. Don’t engage. Delete the message to prevent accidental clicks or forwarding.
What to Do If You Think Your Account Was Compromised
Act fast:
- Change your password immediately.
- Log out of all sessions and remove unknown devices.
- Contact Apptoto Support to lock down your account and review activity.
- Review message history for anything unauthorized.
- Notify clients if it appears hackers sent messages from your account.
If you believe a spammer has accessed private personal or business information, such as passwords, account numbers, etc., visit IdentityTheft.gov to determine what steps to take next. You can also help fight against spam attacks and fraud by reporting attacks at ReportFraud.ftc.gov.
Security Is a Shared Responsibility
Phishing and smishing attacks will only get more sophisticated. But with the right protections and a little bit of caution, you can keep your business and your clients safe.
Apptoto is committed to your security, with tools designed to stop attacks before they spread. But we also encourage you to proactively protect your login, educate your team, and stay alert to scammers’ tactics.
Action Step: Strengthen Your Security Today
🔒 Log in to Apptoto and:
Need help reviewing your setup? Book a quick support call.
Let’s stop phishing and smishing attacks before they start.